Very Basic Engineering
sexta-feira, 11 de março de 2011
Domain Name System
By definition the DNS is the protocol that allows you to use the Internet as it is today. That makes us wonder how were the connections made before that protocol was implemented. I will begin to explain it.
Before the big "boom" of the Internet in the early 90's, there was already connections in networks but they so primitive in comparison with what we have today that it is redundant to try and make a decent approach in terms of comparison. This networks were very small and by being so there was no such requirement for such a protocol to exist, that is because when you wanted to connect with a computer you knew what the computer was and therefore you knew what was the IP of the computer you wanted to connect. So there was only a number of IP's that you needed to know before hand.
This was obliterated by the idea of Internet as we know it today. The engineers needed to come with the solution for the amount of demand, as Internet has the principal idea that everyone from anywhere can access every(*) server and has the right to the information.
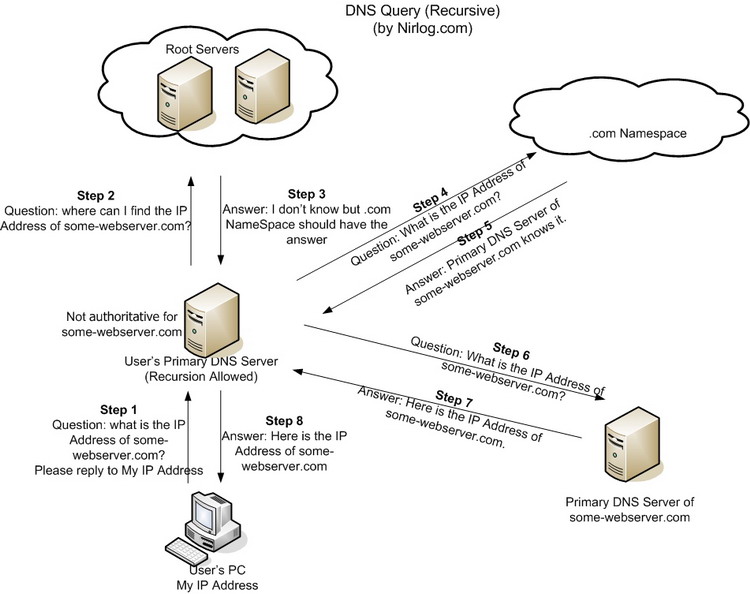
It soon became too difficult for a mere human to know every number of every server, so the solution was the attribution of names, so that you could only type the name of the host that you wanted to connect that the protocol would internally generate the number aggregated to that name.
Sorry for the primitive information but this is merely a very simple analysis of what the DNS is supposed to do.
Here's an image to explain the curious.
Before the big "boom" of the Internet in the early 90's, there was already connections in networks but they so primitive in comparison with what we have today that it is redundant to try and make a decent approach in terms of comparison. This networks were very small and by being so there was no such requirement for such a protocol to exist, that is because when you wanted to connect with a computer you knew what the computer was and therefore you knew what was the IP of the computer you wanted to connect. So there was only a number of IP's that you needed to know before hand.
This was obliterated by the idea of Internet as we know it today. The engineers needed to come with the solution for the amount of demand, as Internet has the principal idea that everyone from anywhere can access every(*) server and has the right to the information.
The most simple example is :
- Imagine to know the IP's of every site that you needed to connect, for eg. 69.63.184.142,...(facebook), 146.201.210.194(Google), etc,etc.
It soon became too difficult for a mere human to know every number of every server, so the solution was the attribution of names, so that you could only type the name of the host that you wanted to connect that the protocol would internally generate the number aggregated to that name.
Sorry for the primitive information but this is merely a very simple analysis of what the DNS is supposed to do.
Here's an image to explain the curious.
quinta-feira, 3 de março de 2011
Security in Networks (basics)
This is a post about the first basis that you need to acquire if you want to do a further studying in Security regarding Networks. First and as you might have seen in movies almost every network that is connected to the Internet has it's flaws and some of the experts that use it can explore them to harm or just access files or information that was not mention for them to see. I have already committed some of the so called "hacking" but notice that I did it with a full academic purpose, in fact that was what got me into studying Informatics Security in the first place, i got so deep(1) and so wide(2) that I was able to see the many errors that the programmers or technicians made in grating such security. I saw so many errors that i felt compelled to change things in my own way and to do so i began my study in informatics security with that purpose.
First i want to address the many stages of doing and implementing in a safe way this security. The baby steps of doing so is addressing what you want to protect by judging which information is the crucial for your network to work accordingly to its purpose, this is made by establishing a number of Politics(3). The other baby step is recognition of how you want do that, this is called Requirements(4).
After this there is only one simple principle(5) that you have to impose in your security and this is acknowledge by almost every one that does Informatics Security.
Definitions :
First i want to address the many stages of doing and implementing in a safe way this security. The baby steps of doing so is addressing what you want to protect by judging which information is the crucial for your network to work accordingly to its purpose, this is made by establishing a number of Politics(3). The other baby step is recognition of how you want do that, this is called Requirements(4).
After this there is only one simple principle(5) that you have to impose in your security and this is acknowledge by almost every one that does Informatics Security.
Definitions :
- Notion of Deepness: Follows a more complex and more efficient security that the perimeter, as the name implies this protection is made by establishing levels of what you want to secure, not regarding the number of Machines that you want to secure.
- Notion of Perimeter: This consist in defining a perimeter that contains a number of machines and networks that you want to secure and avoid the interaction between the two sides of the that perimeter.
- Notion of Politics: As said above it consists in the number of rules that you establish your implementation to have. For explaining i can only demonstrate you some examples, eg. Grating reliability of the information reserved or confidential, eg. Protection of critical information, eg. Continuity of the operation in course or of the service required by the user, etc, etc.
- Requirements: This definition consist in the number of requirements that you need to ensure your politics to that action. eg. Authentication of users or services, eg. Number of privileges of users or services, eg. Keeping track and logging activities, etc, etc.
- Minimum Privilege Principle: The users should use only the rights required for the execution of the tasks that are addressed to them.
terça-feira, 1 de março de 2011
Bomberman
 This will be my first post so I'll do a brief introduction to what this blog will be all bout. I created this blog with the idea to post a little off my work since I am currently studying Computer and Informatics Engineering in ISEL( Engineering of Lisbon Superior Institute ). I will post random works and posts about what I am currently studying in my degree so you may see an awkward discrepancy between posts.
This will be my first post so I'll do a brief introduction to what this blog will be all bout. I created this blog with the idea to post a little off my work since I am currently studying Computer and Informatics Engineering in ISEL( Engineering of Lisbon Superior Institute ). I will post random works and posts about what I am currently studying in my degree so you may see an awkward discrepancy between posts. Having said this I will begin to introduce the the first software. This is the "Bomberman", a game that many of you may have heard, that was asked for us to develop as the last project of the class "Oriented-Object Programming". Notice that it is a development for a class so it definitely has it's bugs and glitches, and any feedback is welcomed.
At last I want to thank Marcos Lamuria and Bruno Oliveira for taking part in the development of this software and for letting me post it on the web.
You can do the download in this link(vb Bomberman).
Note:
To run use "cd c:\....\ src" in the windows command line and then write "java InitWindow".
This should do the trick.
Subscrever:
Mensagens (Atom)